Emad Elshareef
Cybersecurity Consultant
Riyadh, Saudi Arabia
About
With over nine years in Information Security, I serve as a Penetration Testing Team Lead and SME specializing in advanced security assessments across Web, Mobile, API, Application, Active Directory, and Network environments. I integrate technical testing with risk assessment to deliver clear, business-aligned security insights. My work is grounded in key regulatory frameworks, including SAMA CSF and NCA ECC, ensuring both strong security posture and compliance with national standards.
Experience
- Penetration Testing Team Lead @ ConfidentialSA - On-siteSummary:
- Leading a team of cybersecurity consultants in the financial sector, guiding and overseeing highly skilled cybersecurity consultants, directing their efforts towards the enhancement of organizational security.
Responsibilities:
- Leading penetration testing activities across Web, Mobile, API, and Network infrastructures
- Overseeing Active Directory security assessments and vulnerability management
- Directing team efforts towards comprehensive security enhancement initiatives
- Coordinating with stakeholders to ensure security compliance and risk mitigation
Achievements:
- Established comprehensive penetration testing framework for financial services
- Successfully identified and remediated critical security vulnerabilities
- Improved team efficiency and security assessment quality
- Red Teaming
- Penetration Testing
- Web Security
- Mobile Security
- API Security
- Active Directory
- Network Security
- Vulnerability Assessment
- Security Auditing
- Risk Assessment
- Team Leadership
- Sr. Information Security Consultant @ SecurEyesSA - On-siteSummary:
- Senior Information Security Consultant, embarking on a transformative journey characterized by continuous learning and active engagement in diverse security projects.
Responsibilities:
- Conducting comprehensive security assessments and penetration testing
- Providing expert security consulting services to clients
- Developing and implementing security strategies and frameworks
- Mentoring junior security professionals
Achievements:
- Successfully delivered complex security projects
- Enhanced client security postures through expert consultation
- Built strong reputation in the cybersecurity consulting field
- Security Consulting
- Penetration Testing
- Security Assessment
- Client Management
- Security Strategy
- Risk Management
- Sr. Penetration Tester @ GSK Information TechnologySD - On-siteSummary:
- Senior Penetration Tester, learning and working in various security projects, developing expertise in comprehensive security testing methodologies.
Responsibilities:
- Performing comprehensive penetration testing on web applications and networks
- Identifying and documenting security vulnerabilities
- Providing detailed remediation recommendations
- Collaborating with development teams on security improvements
Achievements:
- Successfully identified and helped remediate numerous critical vulnerabilities
- Established testing methodologies and best practices
- Contributed to improved organizational security awareness
- Web App Testing
- Network Testing
- Vulnerability Assessment
- Security Documentation
- Technical Analysis
- Security Tools
- Remote Penetration Tester @ Gateway IT for InnovationSD - RemoteSummary:
- Remote Penetration Tester, first professional role in cybersecurity, spent two years learning and working in various security projects.
Responsibilities:
- Conducting remote penetration testing engagements
- Learning and applying various security testing methodologies
- Documenting findings and providing security recommendations
- Collaborating with remote teams on security initiatives
Achievements:
- Successfully transitioned into cybersecurity profession
- Developed strong foundation in penetration testing
- Established expertise in remote security assessment
- Remote Testing
- Security Fundamentals
- Penetration Testing
- Documentation
- Learning Agility
- Remote Collaboration
- Lecturer @ Cambridge International College SudanSD - On-siteSummary:
- Lecturer in IT Department, working on Information Security Concepts, Web Application Development, and Database Application Development.
Responsibilities:
- Teaching Information Security concepts and principles
- Instructing Web Application Development courses
- Teaching Database Application Development
- Mentoring students in IT and cybersecurity fields
Achievements:
- Successfully educated students in cybersecurity fundamentals
- Developed comprehensive course materials
- Contributed to student career development in IT
- Teaching
- Curriculum Development
- Information Security
- Web Development
- Database Development
- Student Mentoring
- Teaching Assistant @ University Of Science & TechnologySD - On-siteSummary:
- Teaching Assistant in Information Technology Department, beginning of teaching career, learning and working in academic environment.
Responsibilities:
- Assisting professors in Information Technology courses
- Supporting students with coursework and projects
- Conducting laboratory sessions and tutorials
- Grading assignments and providing feedback
Achievements:
- Successfully supported student learning in IT
- Gained valuable teaching and mentoring experience
- Contributed to academic program success
- Teaching Support
- Student Support
- Information Technology
- Academic Research
- Laboratory Instruction
- Assessment
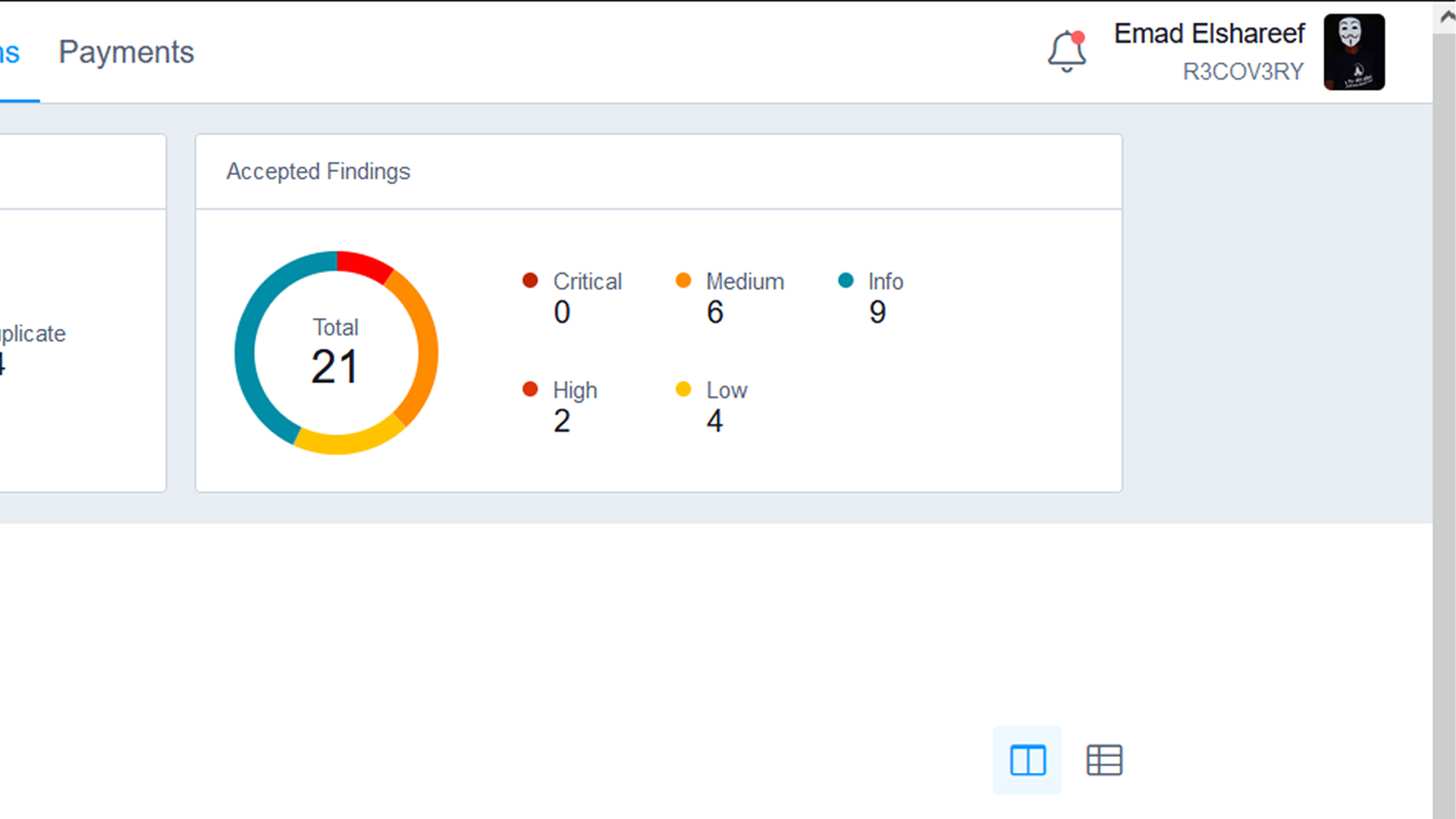
Cybersecurity Journey
Visual highlights from my cybersecurity journey - CTF competitions, bug bounty discoveries, HackerOne achievements, and professional certifications.
Education
University Of Science & Technology
Master of Science (MSc) in Information Technology
University Of Science & Technology
Bachelor of Science (BSc) in Information Technology
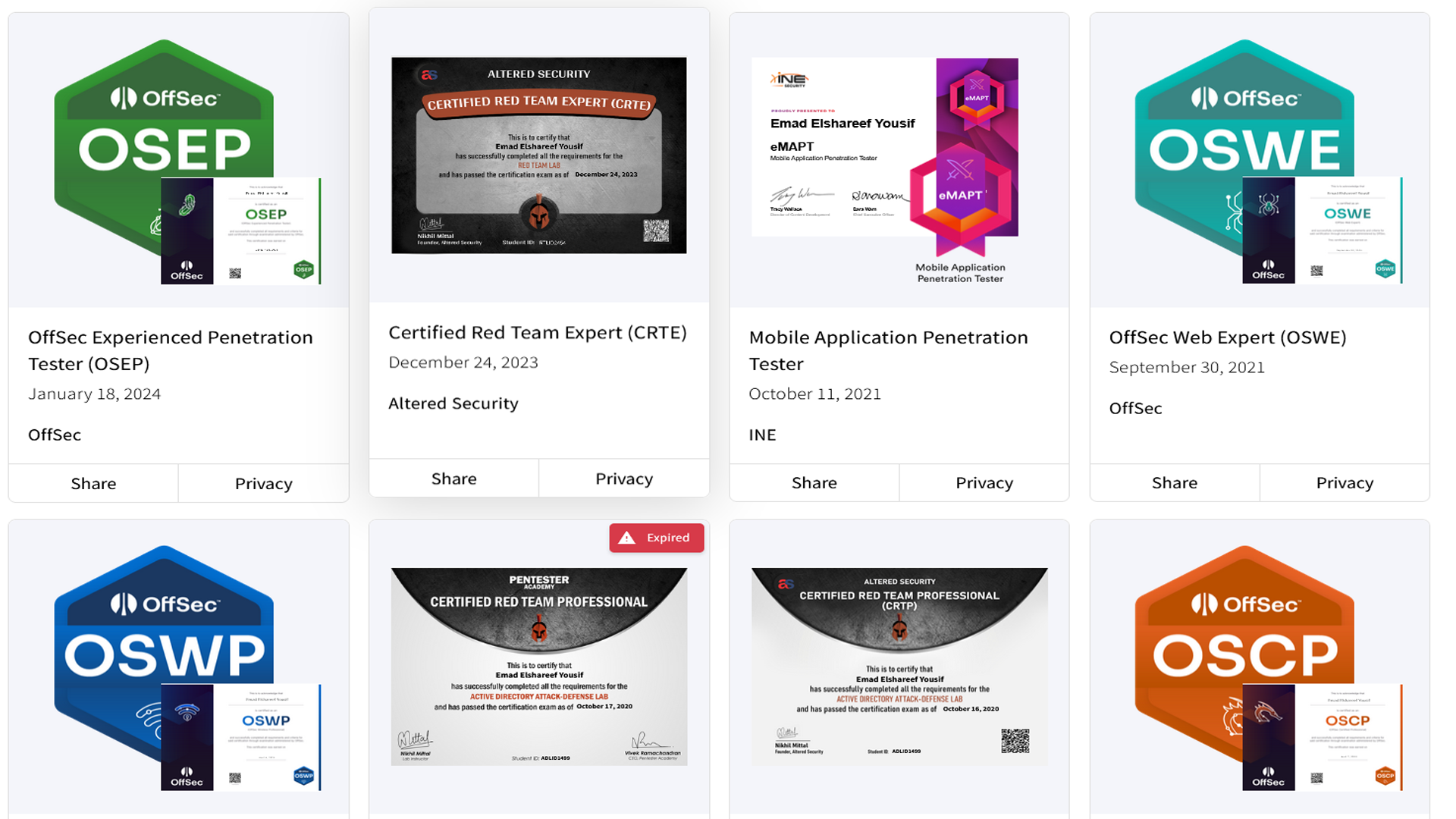
Certificates
Certified Red Team Lead (CRTL)
ZeroPoint Security
Offensive Security Certified Expert (OSCE³)
Offensive Security
Offensive Security Exploit Developer (OSED)
Offensive Security
Offensive Security Experienced Pentester (OSEP)
Offensive Security
Certified Red Team Expert (CRTE)
AlteredSecurity
Certified Red Team Operator (CRTO)
Zero-Point Security
Offensive Security Web Expert (OSWE)
Offensive Security
Offensive Security Wireless Professional (OSWP)
Offensive Security
Certified Red Team Professional (CRTP)
AlteredSecurity
Offensive Security Certified Professional (OSCP)
Offensive Security
Tools & Skills
- Penetration Testing
- Web Application Security
- Mobile Security Testing
- API Security Testing
- Active Directory Security
- Network Security
- Vulnerability Assessment
- Security Auditing
- Comprehensive Risk Assessment
- Burp Suite
- Metasploit
- Nmap
- OWASP ZAP
- Kali Linux
- Python
- PowerShell
- Bash Scripting
- Wireshark
- Team Leadership
- EDR Bypass
- CobaltStrike C2